In the age of dynamic infrastructure, where VMs spin up in seconds and containers vanish in minutes, IP address management (IPAM) has evolved from a networking afterthought into a DevOps-critical responsibility.
If you’re running a hybrid architecture—say, Azure VNets peering into your on-prem data center via ExpressRoute or VPN—then unmanaged IP allocations aren’t just an inconvenience.
They’re a ticking time bomb.
🔻 A single misaligned subnet can:
- Break your site-to-site tunnel
- Cause DNS resolution loops
- Or silently route traffic into the wrong internal segment (hello, security breach 👋)
And in reality? It often starts with something as simple as forgetting which range that test environment claimed two weeks ago.
🚨 This is the modern DevOps challenge: you can scale your infrastructure infinitely, but if you’re not tracking your IPs, you’re scaling blind.
That’s why hybrid cloud demands hybrid IPAM—a system smart enough to integrate with Azure’s dynamic nature, yet strict enough to prevent shadow infrastructure from derailing production.
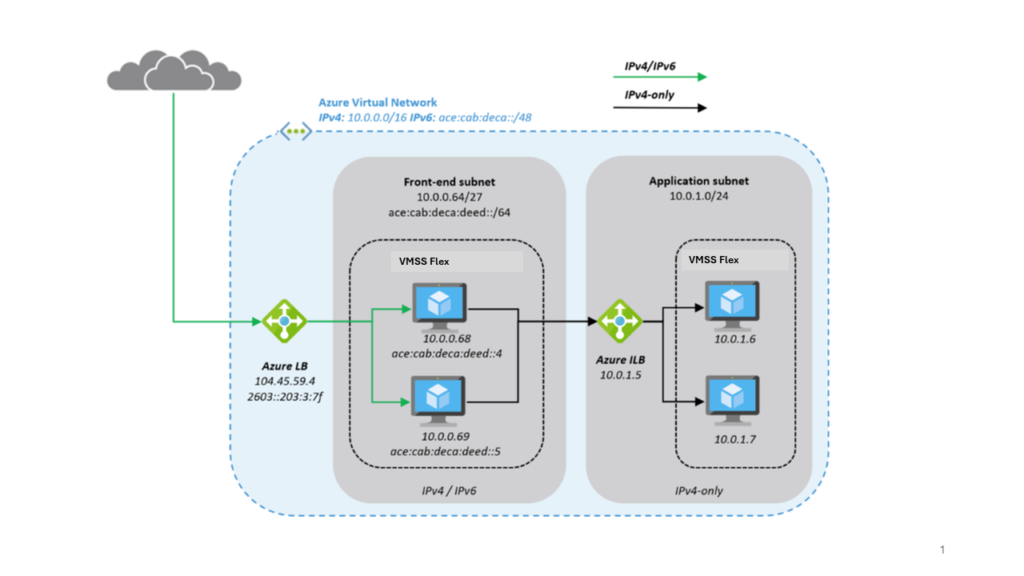
🎯 Why IP Management on Azure Isn’t as Simple as It Looks
Azure VNets and subnets let you allocate IP ranges for resources. Simple, right?
But here’s the catch:
- You deploy VMs, Containers, Functions, Gateways, Load Balancers—each with private/public IPs
- Azure assigns IPs dynamically (unless you pin them)
- You scale horizontally, and suddenly, tracking what owns which IP becomes impossible
- Meanwhile, your on-premises firewall, DNS server, or CMDB still assumes tight IP controls
👉 That’s where IPAM (IP Address Management) steps in—not as a luxury, but as a critical layer of your hybrid cloud foundation
🛡️ Why You Need IPAM in Azure
Traditional on-prem IPAM solutions gave us:
- 📌 Central visibility of used/available IPs
- 🧠 Conflict prevention and subnet planning
- 🔄 DNS integration and DHCP coordination
Azure alone doesn’t offer centralized IPAM. To bridge this gap, you need to integrate Azure with your on-prem IPAM or adopt a cloud-aware IPAM strategy
🔗 Common IPAM Tools Used in Hybrid Azure Setups
Here are some of the most widely used enterprise-grade IPAM platforms:
- Infoblox – DNS/IPAM/DHCP powerhouse with Azure connector support
- BlueCat – Offers a RESTful API and workflow engine
- SolarWinds IPAM – Easy to integrate via scripting and agentless scanning
These tools support integration through APIs, and Azure gives you just enough event-driven and scripting options to plug right in.
⚙️ Integration Strategies: Automating Azure → IPAM Sync
There are two practical patterns for keeping IP allocation synced between Azure and your IPAM:
✅ 1. Real-Time Event-Driven Syncing
Use Azure’s native event pipeline to push updates as they happen:
- Subscribe to Azure Event Grid for events like
Microsoft.Network/publicIPAddresses/writeornetworkInterfaces/write - Hook it to Logic App or Azure Function
- Use HTTP connector or PowerShell core to call your IPAM’s API (e.g.,
POST /ipam/ip)
This approach ensures instant updates—your IPAM is always in sync the moment a resource is provisioned.
✅ 2. Scheduled Inventory Scanning
Ideal for IPAMs without webhook support or air-gapped environments:
- Schedule a PowerShell (or Python) script via Automation Account, GitHub Action, or Task Scheduler
- The script queries Azure for all resources that have an IP address
- Extract metadata: Resource Name, Type, Group, IP, Tags
- Output to
.csvor directly update IPAM via API
Let’s walk through this in a demo.
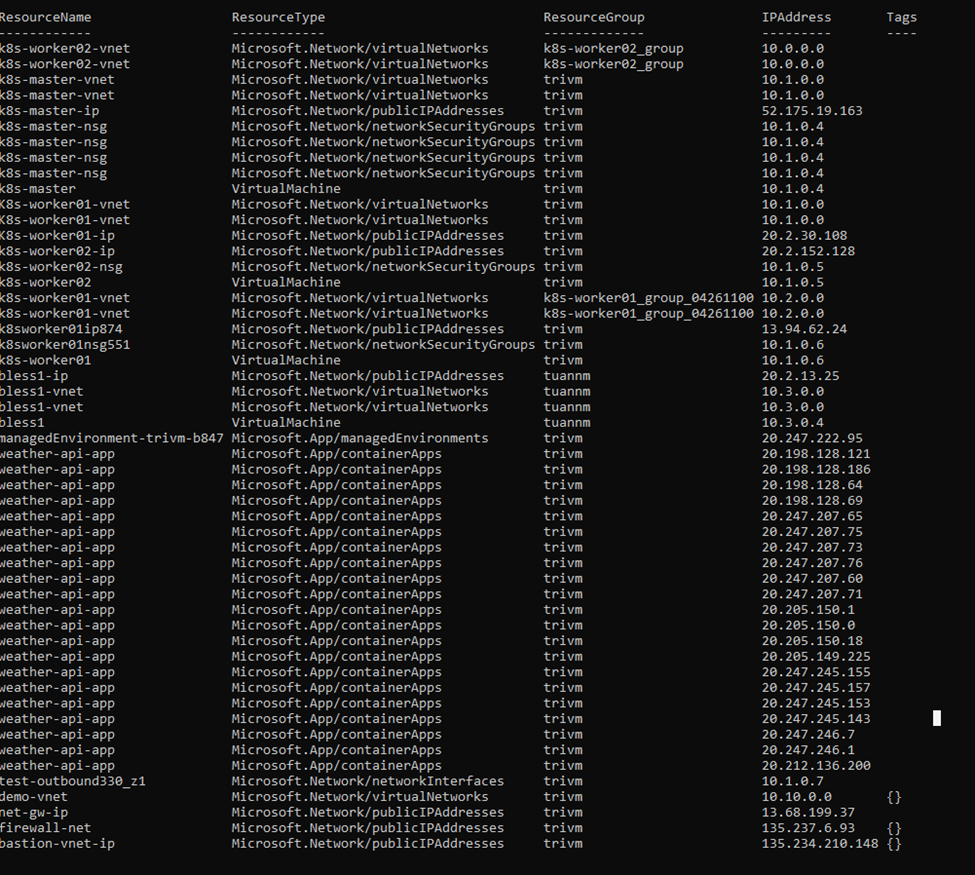
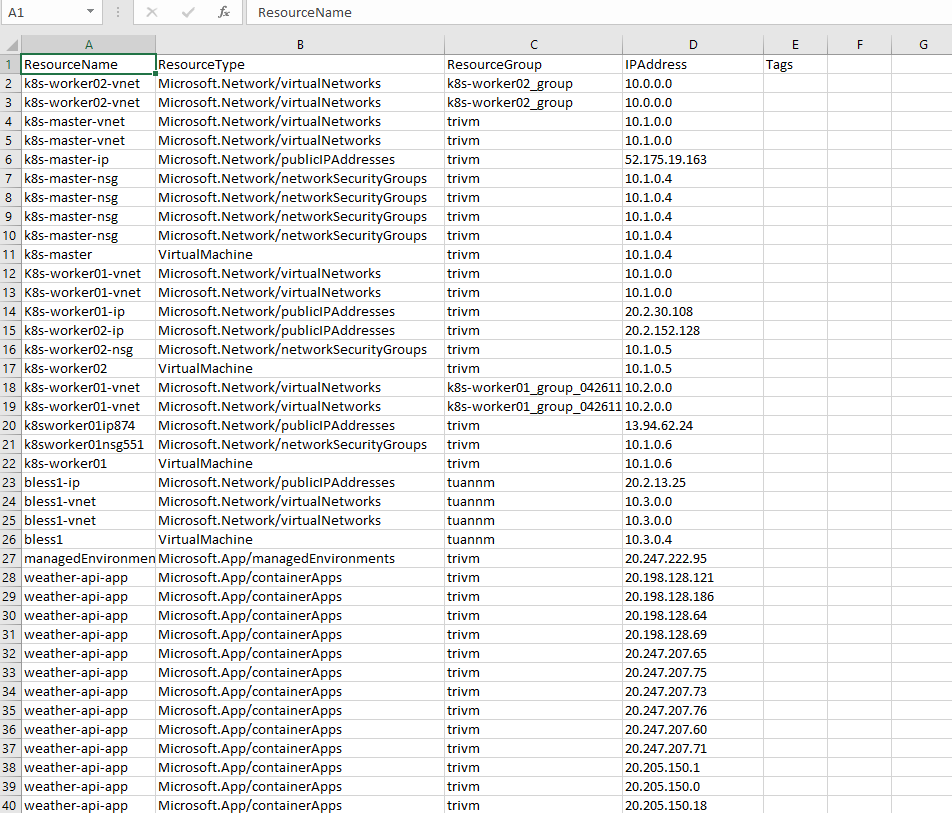
💻 DEMO: Scanning All IP-Bearing Azure Resources
This PowerShell script scans your subscription for any resource with an IP address, including:
- Virtual Machines (via NICs)
- Public IPs
- Application Gateways
- Azure Firewalls
- Container Apps
- Azure SQL (with FQDN resolved to IP)
- Any resource exposing an IP in its
properties
It exports the inventory to Azure_All_Resource_IPs.csv.
📁 Step 1: Clone the repo
git clone https://github.com/vominhtri1991/AzureScanIP.git
cd AzureScanIP🔐 Step 2: Create a Service Principal for Secure Script Authentication
In this step, we’re creating a Service Principal (SP)—an identity your script can use to authenticate to Azure non-interactively (i.e., without manual login or MFA). This is critical for automation, scheduled jobs, or integrations that run in the background.
az ad sp create-for-rbac --name "ipam-export-sp" --role Reader --scopes /subscriptions/<your-subscription-id> --sdk-auth| Parameter | Purpose |
|---|---|
| –name “ipam-export-sp” | Assigns a friendly name to your service principal. This name will appear under App registrations in Azure AD |
| –role Reader | Grants read-only access to Azure resources. This is sufficient for scanning resources and IP addresses without the risk of altering anything |
| –scopes /subscriptions/<id> | Defines the access scope of the SP. Here, it’s scoped to the entire subscription. You can narrow it down to a Resource Group if desired |
| –sdk-auth | Outputs credentials in a JSON format compatible with Azure SDKs and automation tools. This makes it easy to use in scripts |
Save the returned JSON — it includes:
clientIdclientSecrettenantIdsubscriptionId
✍️ Step 3: Paste into script
Open the PowerShell script and replace:
$tenantId = "<tenant-id>"
$clientId = "<client-id>"
$clientSecret = "<client-secret>"
$subscriptionId = "<subscription-id>"🚀 Step 4: Run the script
./ AzureResourcesIPs_ScanToCsv.ps1📊 Sample Output
You’ll see a full dump of IP-related resources in your console and a ready-to-import .csv file.
🧩Conslusion: Don’t Let IP Chaos Sneak Into Your Cloud
🧠 IP sprawl is silent… until it breaks your DNS, confuses your firewall, or blocks a deployment.
In the era of elastic infrastructure and microservices, you can’t afford to lose track of your IPs—especially in hybrid and multi-cloud setups.
🔎 With Azure’s dynamic provisioning model, IP drift happens fast. And without a clear line of sight across your public and private allocations, your automation, security, and compliance posture takes a silent hit.
✅ What You Can Do Today:
- Integrate your Azure environment with a real IPAM system
- Track every IP allocation across VMs, gateways, containers, and more
- Automate updates using Event Grid or scheduled exports
- Feed structured inventory into Infoblox, BlueCat, or any API-capable IPAM
“The cloud gives. IPAM governs.” ☁️👑