In today’s connected world, monitoring devices on your network is a critical part of maintaining strong security. In this post, you’ll learn how to build an automated network monitoring tool using Shell scripting. This tool uses nmap and arp-scan to detect newly connected devices and open ports, and it sends real-time email alerts when unfamiliar devices appear. With a few efficient Bash scripts, you can take proactive steps to protect your network and respond to threats instantly
I. Prepare Script and Set Up Your Environment:
To begin building your automated network monitoring tool, you’ll first need to set up your environment and download the core script.
- Install
arp-scan– This is a lightweight network scanning tool that detects active devices on your local network using ARP requests. On Debian-based systems, use:
# sudo apt update
# sudo apt install arp-scan- Download the Shell Script from GitHub – We’ve created a ready-to-use Bash script that combines
arp-scan, device tracking, and email alerts. You can get it directly from the GitHub repository:
# git clone https://github.com/vominhtri1991/secure-scripting.git✅ The script continuously scans your network for connected devices using ARP. When it detects a new MAC address that isn’t in your trusted list, it instantly notifies you via email with the IP and MAC of the unknown device.
🔧Setup Configuration Files:
- To ensure the script runs correctly and sends email alerts, you need to configure a few essential files:
1/Device Whitelist:
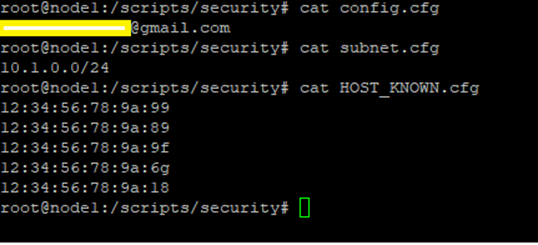
Create a file named HOST_KNOWN.cfg that contains the list of trusted MAC addresses on your network. Each line should include one MAC address in uppercase format, for example:
00:1A:2B:3C:4D:5E
F0:DE:F1:23:45:672/Subnets To Scan:
Create a file named subnet.cfg will include subnet list for scanning new devices connected
3/Email Configuration:
Create a file named config.cfg will include mail using receive warning when has new device connect to your network
II. Configure Email Alerts Using msmtp:
To send email notifications from your script when unknown devices are detected, you’ll use msmtp — a lightweight SMTP client that allows sending emails directly from the command line or scripts.
🔧 Step 1: Install msmtp
# sudo apt-get update
# sudo apt-get install msmtp msmtp-mta🔧 Step 2: Create the Configuration File
– Create config file .msmtprc in home folder of user (user using send mail function). Example root is /root/.msmtprc
#Add below configuration for gmail information
defaults
auth on
tls on
tls_trust_file /etc/ssl/certs/ca-certificates.crt
logfile ~/.msmtp.log
account gmail
host smtp.gmail.com
port 587
from your_email@gmail.com
user your_email@gmail.com
password your_app_password
account default : gmail*Note: password section will be filled in is app passwords (not gmail password) created for gmail by link:
https://support.google.com/mail/answer/185833?hl=en
🔧 Step 3: Test Email Sending
You can test if msmtp is working by running:
(
echo "Subject: Testing Mail MSMTP"
echo "To: recipient@example.com"
echo ""
echo "This is content sending from Bash shell."
) | msmtp recipient@example.com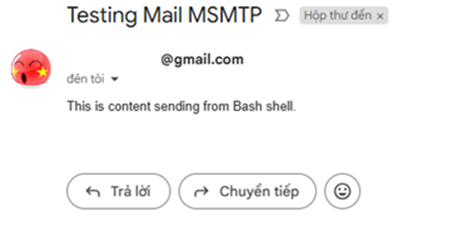
III. Schedule the Script to Run Automatically:
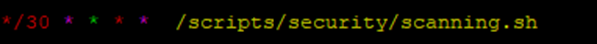
To automate the monitoring process, you’ll use crontab to schedule the script to run every 30 minutes. This ensures your system regularly checks for new devices connected to the network without any manual intervention.
🔧 Step 1: Open crontab editor
# crontab -e🔧 Step 2: Add the following line to schedule the script
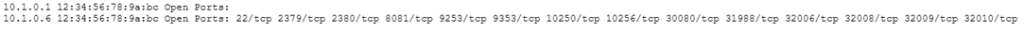
When a new device connects to a subnet listed in subnet.cfg, you will receive an email alert. The message will include the IP and MAC address of the detected device, along with a list of open ports, all attached as a file named new_device.txt